A Toxic Hell Stew of Vulnerabilities
The above quote was made by Tim Cook at last years Apple developers conference in regards to the Android operating system. He went on to say that 99% of all Mobile Malware was produced for, and operated on Android. Having come from a threat research background I can tell you he is not to far wrong. But….
There are lies, damn lies and then, there are statistics. If you just limit your view to a portion of the statistics you could easily conclude the Android is indeed “a toxic hell stew of vulnerabilities”, but that’s only half the picture.
Last week Google released the 2014 year in review for Android Security. It is a pretty interesting read. The guys at Google have significantly improved security features within the Android platform.
For one, Android supports Full Disk Encryption, now they have actually supported this feature for a while, but the password used to protect this encryption could easily be broken using widely avliable exploit tools, such as Scrypt, that would essentially brute force the password. With Android 5.x, the user password is protected against brute force attacks, meaning if you lost your phone and had encryption enabled, your intimate photos will be well protected, well, at least for just over a thousand years it would take current technology to break the encryption.
Android also introduced multi-user mode, including a guest user that is essentially sandboxed from the rest of phone, allowing you to hand your phone over to a friend or foe, comfortable in the knowledge that sensitive data or files are protected. Although Android are in need of some user awareness training to let users know this feature exists and how to use it.
One of the cooler features of Android is one that protects us from afar, the enhanced Google security services for the Android platform. Google Play provides security checks on all applications uploaded to the Play store, to ensure they are not malicious, including all new and upgraded versions of the application. Which is great, IF, all applications came from Google Play, which most do, but not all. There are alternative ways to get Android Apps, especially in countries that are not that enamored by Google, such as China, Russia and Argentina, where Google Play alternatives thrive.

Google Play provides a service called Verify Apps, which has been around for a couple of years and widely adopted in 2013. It will allow the detection of Potentially Harmful Applications (PHA’s) by monitoring their behaviour and looking for suspicious activity when executed. This includes the ability to upload apps installed from outside Google Play.
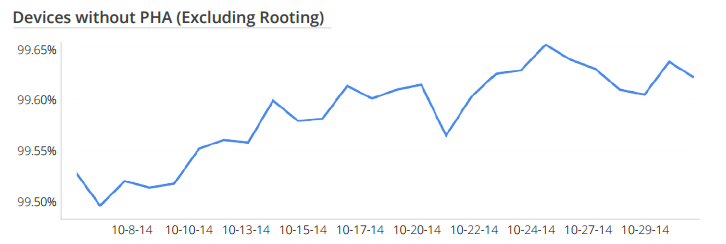
When the guys and gals at Google play analyzed installed apps from across the globe they found that less than 0.5% of ALL Apps were potentially harmful to their users.
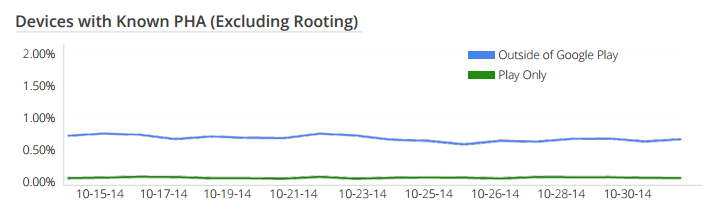
Furthermore the likelihood is that if the application was malicious it was pretty much guaranteed to come from a non-Google Play source.
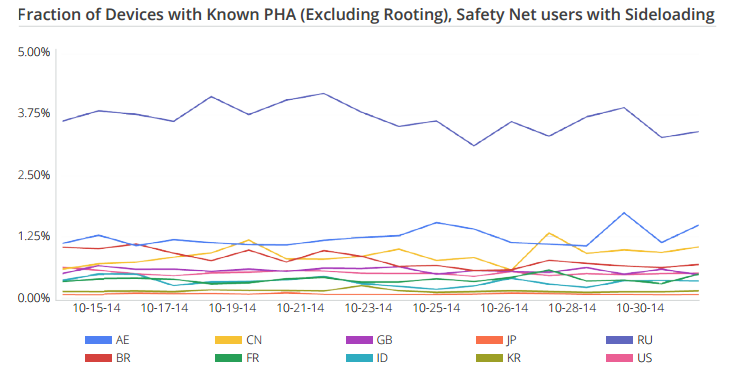
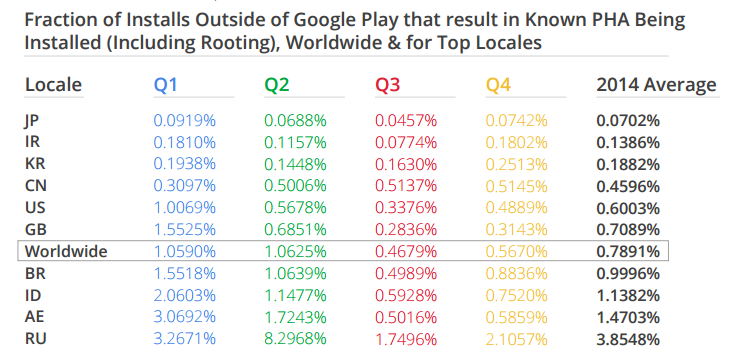
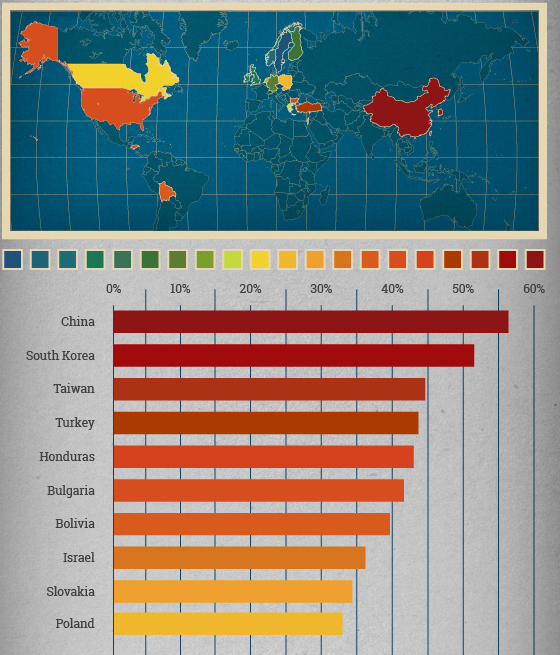
This of course means that the countries with the highest use of non-Google Play market places were more likely to be infected, with Russia, Argentina and China leading the pack.
Even when you analyze the installations of apps sourced from outside of Google Play, which is where most of the risk lies, we are still talking about small percentages, Russia only 3.9%, Argentina less than 1.5% and a worldwide average of less than 0.8% of apps turn up as being malicious.
Now when you multiple those percentages by the billions of Android devices, then the numbers do add up, but when you compare them to PC’s, where it is estimated that between a third (33%) and a half (50%) of all devices are infected with malware then mobile security is stacking up pretty well.
I am not saying don’t pay attention to mobile security, but the truth is the risk is low, especially if your users are only using Google Play for app installs, which lets be honest, most are, especially in western countries. If they are using Apple devices the risk is even lower.
If you have security budget to spend, ICS devices, PC’s and servers would be a better target for your budget.
Below graphics from Microsoft and Panda Security.