It seems the so called “Next-Gen AV” companies can be a little sensitive. A security researcher and red teamer, Curtis Brazzell, was practicing his skills against one of these so called next-gen Anti-Virus products, trying to bypass their built in protections to either shut down the AV service or stop it from being useful.
After popping a shell on the box he wanted to use what tools he had available to him locally to bypass the protections. Running as Admin he was unsuccessful in stopping the service, so elevated his privileges to System user, using psExec.
He was then able to make progress, first he was able to set the service startup to “disable”, meaning on a reboot the “next-gen AV” would be useless. But was struggling to kill the process. He tried a bunch of steps such as injecting junk in to the process in an attempt to get the process to crash and die. Not luck. What did work however was deceptively simple.
All that was required was to use his elevated system privileges to “move” the anti-virus binaries to a different location, the so called “next-gen av” was still running, just not functioning, meaning you can now drop any trojan, virus or malware on to the boxed. Owned!
He didn’t stop there, next he was also able to disable the AV Service and move the binaries remotely as SYSTEM user, across the entire Domain! Basically, he was able to pawn any organisation on the planet that has this so called “next-gen AV” but popping a single shell in the network. Ouch!
Now this would normally mean Curtis would get a pat on the back by the community, the next gen AV would fix their issues and it becomes a learning experience for everyone involved. But no, the so called next-gen AV company was not happy.
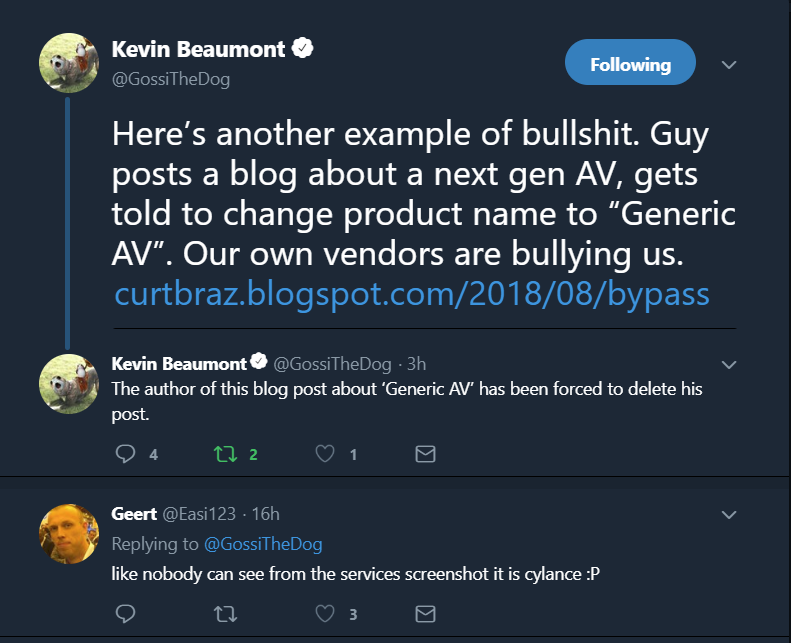
First they insisted that the blog explaining details of his fantastic research remove all reference to their name. Resulting in him referring to them as “Generic-AV” (which seems like a bit of insult to generic AV’s if you ask me).
Then it gets worse, he gets “forced” to take the blog down entirely. What the actual fu*k?
Of course this is not the first time a researcher has been bullied to take down their content. SentinelOne put in a request to YouTube to take down James Williams presentation titled “Next-Gen Av vs My shity code”. Where he was able to demonstrate the limitations of a number of “next-gen AV” products. (The video has since returned and can been seen at the bottom of this article.)
If your product is so shite that you need to bully people who point out the weaknesses, maybe you need to work on your product? Just a thought. For what it is worth here is a link to the Blog in case the so called “Next-Gen Av” comes to their senses and allows Curtis to put the blog back up.