Incident response plans often stumble when a breach hits because they rely on ideal conditions that rarely exist. Teams face incomplete data, unclear roles, and intense pressure, which turns a static playbook into chaos. By testing realistically, defining clear escalation, and weaving business continuity into every step, you can turn those weak spots into a resilient defense.
Common Pitfalls That Crumble Plans
- Lack of Real‑World Testing – Table‑top drills and live simulations expose gaps static documents hide.
- Undefined Roles and Escalation Paths – When senior staff are unavailable, unclear authority leads to paralysis.
- Over‑Reliance on Perfect Data – Plans must still work with noisy, partial logs.
- Insufficient Communication Protocols – Stakeholder updates need pre‑scripted flexibility.
- Neglecting Business Continuity Integration – Recovery isn’t just IT; the whole business must keep moving.
- Failure to Update the Plan – Threat landscapes evolve, so should your playbook.
- Ignoring Post‑Incident Learning – Without a thorough after‑action review, the same mistakes repeat.
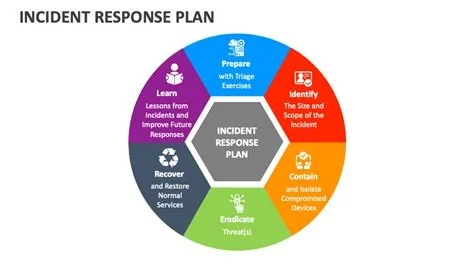
10‑Step Framework to Strengthen Your IR
1. Governance and Preparation
Establish clear ownership, define objectives, and gather threat intelligence before an incident occurs.
2. Detection and Triage
Implement monitoring that flags anomalies early and assign a triage team to assess severity.
3. Containment
Isolate affected systems quickly while keeping business‑critical services running.
4. Eradication
Remove malicious artifacts and verify that the threat is fully eliminated.
5. Recovery
Restore systems to normal operation, validate integrity, and monitor for relapse.
6. Post‑Incident Review
Conduct a root‑cause analysis, document lessons learned, and update the playbook.
7–10. Continuous Improvement
Integrate metrics, refine communication templates, align with business continuity, and schedule regular rehearsals.
Actionable Steps You Can Take Today
- Run a tabletop exercise this week that simulates incomplete data and leadership pressure.
- Map a clear escalation matrix with backups for every critical role.
- Embed a business‑continuity checklist into your IR playbook to align recovery with service level agreements.
- Schedule a post‑incident review after any security event, no matter how minor, and record the findings.
Why It Matters for Your Business
When you master incident response, you limit downtime, avoid regulatory penalties, and protect customer trust. Rapid containment can slash financial loss, and transparent communication often boosts brand loyalty. Insurers also look for proven IR capabilities before underwriting cyber‑insurance, so a solid plan can lower your premiums.
Ready to put your plan through its paces? The clock’s already ticking, and the next test could be tomorrow.