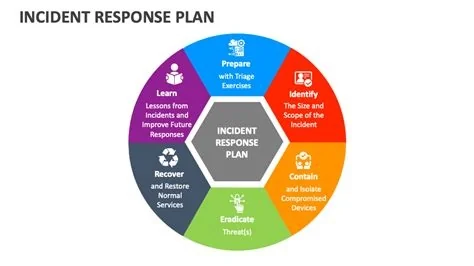
An incident response plan that crumbles under pressure can cost millions, but a streamlined, practice‑driven plan keeps breaches under control. To build a plan that holds, simplify procedures, define crystal‑clear roles, integrate vendor contacts, automate key actions, run regular drills, secure executive backing, and turn every post‑mortem into a playbook update. Follow these steps and you’ll cut response time dramatically.
Root Causes of Plan Collapse
Complex Steps Slow Decision‑Making
When a playbook contains dozens of optional actions, analysts waste precious seconds hunting for the right one. Under attack, the brain defaults to the simplest path, which often isn’t the documented one.
Unclear Roles Create Bottlenecks
If team members aren’t sure who has authority to approve containment, escalation stalls. Ambiguity fuels hesitation, and attackers exploit every pause.
Vendor Coordination Is Frequently Overlooked
Most incidents involve third‑party services—cloud providers, MSSPs, forensic labs. Without pre‑approved contact trees, you end up scrambling for phone numbers while the breach spreads.
7 Fixes to Strengthen Your Incident Response
- Simplify procedures – Keep each action to a single, clearly labeled step. If it takes more than a few minutes to locate, it will likely be skipped.
- Define crystal‑clear roles and escalation paths – Assign ownership for detection, containment, eradication, and recovery. Publish a one‑page hierarchy that everyone can reference instantly.
- Integrate vendor coordination – Build a contact matrix for all critical providers, test the links quarterly, and embed the matrix in your automation scripts.
- Automate repeatable actions – Deploy SOAR or similar tools to launch containment scripts, isolate endpoints, or block malicious IPs without manual clicks.
- Run regular tabletop and live‑fire drills – Practice the exact steps you expect to take. Real‑time simulations reveal hidden gaps and build muscle memory.
- Secure executive sponsorship – Ensure leadership understands the financial impact of a slow response and allocates budget for training, tooling, and continuous improvement.
- Document lessons learned – After every incident, conduct a post‑mortem, capture what worked and what didn’t, and feed those insights directly back into the playbook.
Impact of a Strong Plan
When your team can act swiftly, the window for data exfiltration shrinks dramatically, reducing potential fines and reputational damage. A lean plan also eases the burden on SOC analysts, who are already battling alert fatigue, allowing them to focus on high‑value decisions instead of hunting for paperwork.
Keeping the Plan Alive
Continuous improvement is the only way to stay ahead of evolving threats. Schedule quarterly reviews, update vendor contacts after any contract change, and refresh automation scripts whenever new attack techniques emerge. By treating your incident response plan as a living, battle‑tested capability, you turn each breach into an opportunity to sharpen your defenses.
Future‑Proofing Your Response Strategy
Threat actors are increasingly leveraging AI and supply‑chain attacks, which means static, document‑heavy playbooks will become obsolete. Embrace a dynamic approach: integrate threat‑intel feeds, automate decision points, and maintain a culture of relentless practice. If you adopt these habits today, you’ll not only survive the next breach—you’ll gain a competitive edge.