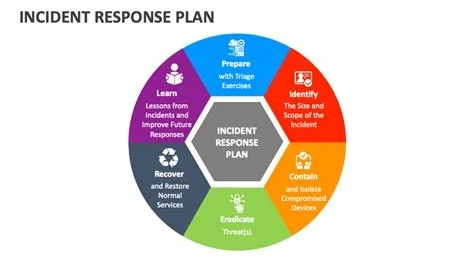
An Incident Response Plan (IRP) fails when teams can’t activate it fast enough under stress. The main culprits are unclear escalation steps, stale contact data, and a lack of realistic practice. By tightening communication protocols, keeping contact lists current, and rehearsing drills regularly, you can turn a static document into a rapid‑response engine.
Common Reasons IRPs Collapse Under Pressure
Vague Escalation Paths
When an alert fires, teams scramble if they don’t know who should take charge. Ambiguous hand‑off rules cause delays, increase confusion, and let attackers gain ground.
Outdated Contact Information
Contact lists that haven’t been refreshed in months leave on‑call engineers unreachable. The result? Critical minutes wasted trying to locate the right person.
Lack of Real‑World Practice
Paper‑only procedures feel safe until a real incident hits. Without regular tabletop or red‑team exercises, staff rely on memory instead of muscle‑memory, and the plan stalls.
Proven Fixes to Strengthen Your IRP
Define Clear Escalation Protocols
Map every alert tier to a specific owner and set explicit timeframes. Document who does what, when, and how so the chain of command is unmistakable.
Keep Contact Lists Fresh
Schedule a quarterly audit of on‑call rosters, Slack channels, and phone numbers. Automate reminders to update entries whenever personnel changes occur.
Conduct Regular Tabletop and Red‑Team Drills
Simulate realistic scenarios—phishing, ransomware, insider misuse—and run them at least once every three months. These rehearsals embed the plan into your team’s instinct.
Automate Playbooks with SOAR
Leverage Security Orchestration, Automation & Response platforms to trigger predefined actions automatically. Automation removes the “who does what” guesswork during a crisis.
Quick Action Checklist for Leaders
- Verify that detection tools feed directly into your IRP workflow.
- Ensure escalation paths are documented and visible to every responder.
- Update on‑call rotation lists and communication channels quarterly.
- Schedule and execute a tabletop exercise for a high‑impact threat each quarter.
- Deploy a SOAR playbook that automates initial containment steps.
- After each incident, hold a post‑mortem that captures both successes and gaps.
- Feed lessons learned back into the IRP to keep it a living document.
Practitioner Insight
One senior incident manager shared that after a full‑scale simulation, the team discovered an outdated on‑call list. Updating the list was quick, but the real win came when their Slack‑based incident bridge handled a real ransomware attempt without a hitch, containing the threat in under two hours. This experience proves that regular practice turns procedures into instinct.
What You Can Do Right Now
Start by auditing your current IRP against the checklist above. Then, set a calendar reminder for the next tabletop drill and assign ownership for contact‑list maintenance. Finally, explore a SOAR solution that fits your stack and automate at least one containment step today. By taking these actions, you’ll move from a static compliance document to a dynamic defense mechanism that can survive any cyber‑storm.