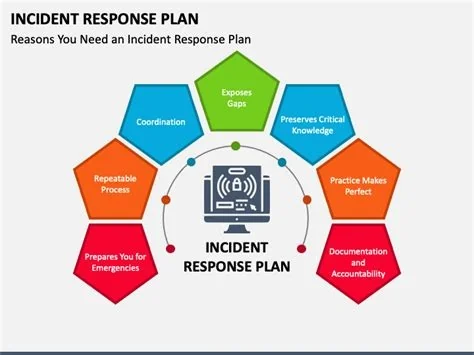
An incident response plan (IRP) fails when it stays static, lacks clear ownership, and never gets tested. To keep downtime, reputation loss, and legal exposure at bay, your IRP must be a living document that reflects real risks, assigns accountable roles, and integrates with business continuity. Below you’ll learn the seven traps that sabotage plans and the exact steps to fix them.
Why Plans Collapse Under Pressure
- Out‑of‑date playbooks – Documents that haven’t been refreshed in months become irrelevant when new threats emerge.
- No clear owner – When nobody is accountable for updates, the plan drifts into oblivion.
- Insufficient training – Teams that never practice their roles stumble during an actual incident.
- Poor communication channels – Alerts lost in endless email threads delay response.
- Unclear escalation criteria – Without defined triggers, senior help arrives too late.
- Lack of business‑continuity integration – Recovery steps that ignore dependencies cause cascading failures.
- Missing lessons‑learned loop – Post‑mortems that aren’t fed back into the plan repeat the same mistakes.
Turning Your IRP into a Living Document
Start by mapping the specific risks your organization faces—whether ransomware, data loss, or physical threats. Then, embed a schedule for quarterly reviews and assign a dedicated owner who can drive updates. This habit keeps the plan aligned with evolving technology and regulatory expectations.
Adopt a Command Structure Inspired by SRE
Borrow the clear hierarchy used in Site Reliability Engineering: an incident commander, a communications lead, a technical lead, and supporting roles. Each role carries explicit responsibilities, so when a breach hits, everyone knows who to call and what to do. Even small teams can benefit from this simple, role‑based framework.
Test, Refine, and Repeat
Testing isn’t a one‑off event. Run tabletop exercises that simulate realistic attack scenarios, then conduct live drills to validate alert routing and decision‑making. After each exercise, capture findings in a “lessons‑learned” repository and update the playbook accordingly. You’ll see faster containment and lower remediation costs over time.
Integrate Business Continuity for Full Protection
Incident response and business continuity are two sides of the same coin. Align recovery steps with your organization’s critical processes—such as finance, supply chain, and customer support—to avoid gaps that could cripple operations. When auditors see a coordinated approach, they’re more likely to trust your resilience.
Leverage Managed Services Wisely
Managed detection and response (MDR) providers can augment your internal capabilities, but they work best when plugged into a mature IRP. Define clear hand‑off points, set expectations for rapid detection, containment, and recovery, and ensure the service feeds its insights back into your plan.
Key Takeaways for Building an Effective IRP
- Keep the playbook current with a scheduled review cadence.
- Assign a single owner responsible for updates and training.
- Use a clear command hierarchy so every team member knows their role.
- Run regular tabletop and live drills; capture lessons learned each time.
- Integrate incident response with broader business‑continuity strategies.
- Make sure managed services complement, not replace, your internal processes.
By treating your incident response plan as a dynamic, organization‑wide discipline, you’ll not only survive breaches—you’ll emerge with your reputation intact. Ready to upgrade your IRP? Start with one of the fixes above and watch your resilience grow.