Regulators now demand that incident‑response programs deliver sub‑hour detection, immutable documentation, and proven execution, turning speed into a legal requirement. To stay compliant, organizations must replace static checklists with dynamic, automated drills that record every action and integrate third‑party vendors. Missing these standards can trigger fines, reputational harm, and even criminal liability for executives.
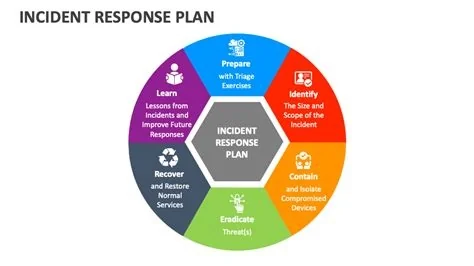
The Three Pillars Regulators Enforce
Speed: Sub‑Hour Detection and Containment
Authorities require measurable detection and containment within minutes, not hours. Your security team needs real‑time alerts that automatically trigger isolation scripts, so you can meet the statutory window without manual delay.
Documentation: Immutable, Timestamped Logs
Every decision, command, and communication must be captured in tamper‑proof logs. Using write‑once storage or blockchain‑based ledgers ensures auditors can verify the timeline without dispute.
Demonstrable Execution: Live, Rehearsed Processes
Having a PDF on a shared drive isn’t enough. You must prove the plan works under pressure through regular, realistic drills that involve all stakeholders.
Common Pitfalls That Sabotage IR Plans
- No clear ownership: When an alarm sounds, nobody knows who takes charge.
- Out‑of‑date contact lists: Vendors and legal counsel become unreachable when you need them most.
- Ignoring third‑party integration: Cloud providers and SaaS partners are often the attack vector, yet many plans treat them as afterthoughts.
- Insufficient testing: Tabletop exercises don’t simulate the chaos of a live breach.
- Static documentation: PDFs don’t update when new threat intel arrives.
Five Must‑Have Features for a Battle‑Ready IR Plan
- Dynamic run‑books: Pull real‑time threat intel and automatically adjust play‑steps.
- Automated evidence collection: Scripts snapshot logs, memory dumps, and network traffic the instant an alert fires.
- Integrated communication hub: A secure channel notifies internal teams, legal, PR, and pre‑approved third‑party contacts simultaneously.
- Version‑controlled repository: Think Git for IR procedures, tracking every change and allowing rollbacks.
- Continuous rehearsal: Weekly red‑team vs. blue‑team drills stress‑test the entire workflow from detection to post‑mortem.
Practical Steps to Cut Containment Time
- Map every data flow: Even innocuous API calls can become breach entry points.
- Embed vendor SLAs into the run‑book: Automatic escalation triggers when a third‑party service shows anomalous behavior.
- Leverage immutable logging services: Write logs to a write‑once, cloud‑based ledger to keep evidence tamper‑proof for audits.
By adopting these five features and eliminating common pitfalls, you’ll meet the new regulatory windows, limit financial fallout, and preserve customer trust. In short, a dynamic, automated, and continuously exercised incident‑response program isn’t just a compliance checkbox—it’s your best defense against the next breach.