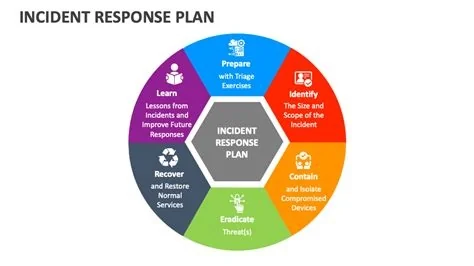
Incident response plans often look solid on paper, but under real attack they can fall apart. The main reasons are overly complex steps, unclear roles, and missing coordination with vendors. By simplifying procedures, defining clear escalation paths, and rehearsing drills regularly, you can turn a brittle plan into a reliable defense that works when you need it most.
Why Plans Crumble Under Pressure
- Incomplete or conflicting information – During an active breach, data streams are noisy and alerts can contradict each other.
- Leadership pressure – Executives demand answers fast, pushing responders to decide with half‑baked facts.
- Unclear scope – The impact radius can shift in minutes, turning a localized outage into a company‑wide crisis.
- Simultaneous technical and business disruptions – Engineers fight a compromised server while finance teams scramble to assess exposure.
- Limited personnel availability – Key responders may be on vacation, in another time zone, or overwhelmed by alerts.
- Complex, poorly structured playbooks – When a plan reads like a legal contract, responders hesitate, unsure of who does what.
- Missing third‑party coordination – Vendors have their own response processes; without alignment, hand‑offs become bottlenecks.
Essential Fixes for a Resilient IR Plan
Simplify the Playbook
Strip procedures down to essential decision points. Use clear flowcharts that can be scanned in seconds instead of dense text.
Define Precise Escalation Paths
Map who contacts whom at each severity level and embed that map directly into your ticketing system. This removes guesswork when the clock is ticking.
Run Realistic Simulations
Table‑top exercises and red‑team drills should mimic the chaos of a real attack: incomplete logs, conflicting alerts, and senior‑leadership pressure. Regular practice turns protocols into muscle memory.
Integrate Vendors Early
Establish joint response agreements, share contact trees, and test cross‑organization communication before a breach occurs. Treat third‑party teams as extensions of your own.
Assign Backup Responders
Ensure every critical role has a secondary owner who can step in instantly. Document these backups in the same place as the primary assignments.
Maintain a Living Document
After each drill or real incident, capture lessons learned and update the playbook. A static PDF quickly becomes obsolete; a living document stays relevant.
Immediate Actions You Can Take
- Condense your current IR playbook to one‑page flowcharts.
- Embed the escalation matrix into your incident ticketing tool.
- Schedule a 15‑minute “quick‑fire” simulation this week.
- Reach out to your top three vendors and set up a joint response call.
- Identify backup owners for each responder role and add them to the contact list.
- Create a short “lessons learned” template to fill out after every exercise.
Practitioner Insight
“During our last tabletop we discovered the escalation matrix was hidden in a SharePoint folder no one could find under pressure,” says a senior SOC manager. “We moved it into our ticketing platform, run weekly quick‑fire drills, and now the team can name the next owner without hesitation. The difference is night and day when a ransomware event hits.”