When a breach hits, you need an incident response plan that works under pressure, not just on paper. A resilient plan focuses on clear escalation, streamlined phases, real‑time vendor coordination, regular drills, and rapid lesson capture. By tightening these core features, you turn a brittle checklist into a battle‑tested defense that protects your brand and operations.
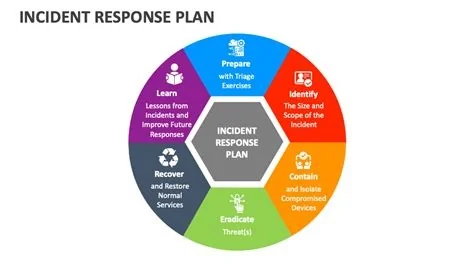
The Six‑Phase Blueprint
Effective response follows a logical lifecycle. Treat each phase as a living workflow, not a static list.
- Preparation – Assemble the team, define roles, and inventory critical assets before an incident occurs.
- Identification – Spot anomalies early and confirm whether they constitute a genuine incident.
- Containment – Isolate affected systems to halt lateral movement and limit damage.
- Eradication – Remove the attacker’s foothold and any lingering artifacts.
- Recovery – Restore services safely while monitoring for re‑infection.
- Lessons Learned – Conduct a post‑mortem, update the plan, and train again.
Integrating Vendors and the Supply Chain
Modern attacks often travel through a supplier’s software or cloud service. Your response must include external partners as if they were internal teammates.
- Embed vendor contacts and service‑level agreements directly into each phase.
- Schedule joint drills with key suppliers to test coordination under real‑time pressure.
- Maintain an up‑to‑date vendor playbook that outlines escalation paths and communication channels.
Why Plans Falter Under Pressure
When the heat is on, common pitfalls surface quickly.
- Complex, undocumented steps – Teams can’t navigate a maze of procedures during an emergency.
- Unclear ownership – If two people think the other is leading, nothing gets done.
- Poor communication channels – Email threads drown in alerts; instant messaging is missing.
- No vendor playbook – External partners are left out of the loop.
- Lack of regular drills – Theory never translates to practice without rehearsal.
- Insufficient business continuity overlap – Recovery plans ignore critical business functions.
- Failure to capture lessons – Repeating the same mistakes becomes inevitable.
What Business Leaders Must Consider
Beyond IT, a weak response plan threatens brand reputation and regulatory compliance. You should ask yourself whether your vendors’ response capabilities match your own and ensure that the plan aligns with broader business continuity goals.
Practitioner Insights
Security professionals report that a “perfect” document quickly becomes a paperweight during a ransomware attack. Simplifying steps, assigning a single escalation owner, and running tabletop exercises with cloud providers make the difference between chaos and control.
Actionable Steps to Strengthen Your Plan
- Trim the playbook – Remove redundant steps; keep the flow intuitive.
- Define a single escalation owner – One person calls the shots, others follow.
- Map vendor contacts into every phase – Treat them as internal teammates.
- Schedule quarterly drills – Include both technical and business continuity scenarios.
- Document lessons immediately – Update the plan while the incident is still fresh.
By treating incident response as a living, collaborative drill rather than a static binder, you’ll turn a brittle defense into a reliable shield. The next time a breach tries to breach your walls, you’ll be ready—not just on paper, but in the heat of the moment.