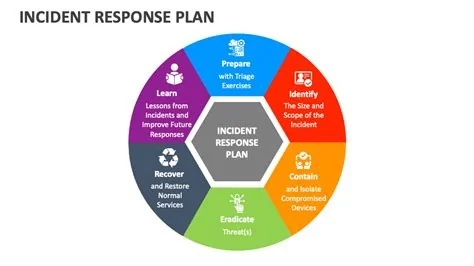
An incident response (IR) plan that only lives on a shared drive crumbles the moment a breach hits. Without clear escalation paths, rehearsed communication, and real‑time run‑books, teams waste minutes and risk millions in losses. This guide shows the core features that keep your IR plan functional and explains how to turn a static document into a battle‑tested process you can rely on.
Why Plans Collapse Under Pressure
When a cyber‑attack strikes, vague escalation routes and unpracticed communication turn a coordinated effort into chaos. Teams often forget who to call, which channel to use, or how to hand off evidence, leading to costly delays. Add regulatory expectations for rapid containment and documented evidence, and a weak plan can cost millions per hour.
Vague Escalation Paths
Without predefined, regularly‑tested escalation matrices, responders scramble to identify the right contacts. The result is a disjointed response that wastes precious minutes. Mapping who gets notified at each severity level—and backing up each contact with an alternative—creates a clear, repeatable chain of command.
Communication Not Muscle Memory
One‑off tabletop exercises aren’t enough. When communication protocols aren’t rehearsed weekly, teams lose the rhythm needed for swift action. Embedding secure chat, phone trees, and scripted dialogue into regular “fire drills” turns coordination into muscle memory.
Financial and Regulatory Stakes
Industry surveys show that organizations lose an average $2 million per hour when IR plans fail, totaling $76 million annually. Regulators across major regions now demand documented evidence of every response step. Failing to meet these expectations can trigger hefty fines, legal exposure, and lasting reputational damage.
Key Gaps That Kill Your Response
- Unclear ownership of response tasks
- Missing or outdated run‑books
- Insufficient logging and evidence collection
- Delayed decision‑making processes
- Poor coordination with third‑party vendors
- Weak post‑incident analysis procedures
- Inadequate governance and metric tracking
Transforming Your Plan into a Live Process
- Live run‑books – Convert static documents into interactive, version‑controlled playbooks that auto‑populate ticket numbers, asset IDs, and contact lists.
- Continuous simulation – Replace annual tabletop sessions with weekly fire drills that rotate scenarios, involve red‑team adversaries, and include external partners.
- Clear escalation matrices – Define who is notified at each severity level, add backup contacts, and pre‑select secure communication channels.
- Metrics‑driven governance – Track mean time to detect (MTTD), mean time to respond (MTTR), and post‑incident review completion rates to enforce accountability.
- Supply‑chain liaison roles – Assign a dedicated point of contact for each critical vendor and embed vendor‑specific response steps into the main IR workflow.
Live Run‑books in Action
When a breach is detected, the live run‑book pulls the incident ticket into the playbook, fills in affected asset details, and notifies the escalation matrix automatically. This eliminates manual data entry and speeds up containment.
Continuous Simulation Benefits
Weekly drills keep your team’s response instincts sharp. Teams that adopt this rhythm report up to a 40% reduction in MTTR, because they’ve practiced the exact steps they’ll need during a real event.
Supply‑Chain Coordination
Embedding vendor response clauses ensures you know exactly how to request forensic data, coordinate public disclosures, and align timelines with third‑party partners. Organizations that do this see a 30% drop in escalation delays during supply‑chain incidents.
Take Action Now
Stop treating your IR plan as a paper tiger. Start converting it into a dynamic, rehearsed process that you can trust when the clock is ticking. By tightening escalation paths, automating run‑books, and practicing communication every week, you’ll protect your organization from costly downtime and regulatory penalties. Are you ready to put the drills in, the run‑books live, and the escalation paths crystal clear?