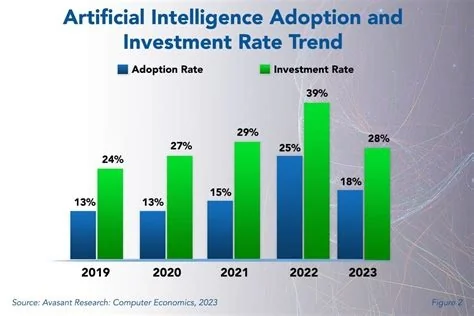
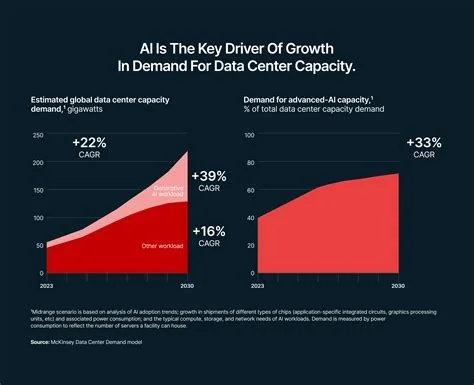
Clawdbot is a self‑hosted AI assistant that integrates with messaging platforms such as WhatsApp, Telegram and Slack to automate emails, calendar events, reminders, and web tasks. Powered by a local large language model with persistent memory, it provides developers a customizable “digital employee” while prompting serious questions about security, credential exposure, and permission controls.
What Clawdbot Does
Core Productivity Functions
Clawdbot can read, summarize, and reply to emails, manage calendar entries, create reminders, and sync with tools like Notion and Todoist. Its browser‑automation layer logs into websites, fills forms, and posts updates without additional prompting.
Cross‑Platform Context Retention
The assistant maintains a “second brain” that stores conversation embeddings in a vector‑store database, allowing context to persist across days and switch seamlessly between platforms (e.g., continuing a chat from WhatsApp on Telegram).
Proactive Automation
Users can schedule morning briefings, monitor dashboards, track stock prices, or trigger custom scripts that interact with APIs and manage server infrastructure.
Rapid Adoption
Within days of release, Clawdbot gained strong traction among developers who appreciate its quick setup and hardware‑agnostic design, which works on typical Windows PCs as well as other operating systems.
Technical Foundations
Modular Architecture
The assistant combines a locally run large language model with open‑source automation libraries. Automation relies on tools such as Selenium for web interaction and custom Python scripts for API calls.
Persistent Memory Store
Conversation embeddings are indexed in a vector‑store database, enabling cross‑session recall and context continuity.
Extensible Plugin Ecosystem
Community‑driven plugins add support for additional calendars, CRM systems, and home‑automation devices, expanding Clawdbot’s capabilities beyond its core features.
Safety Concerns
- Credential Exposure: Misconfigured files can leak sensitive information when the assistant runs on user‑controlled hardware.
- Autonomous Actions: The ability to send emails, post on social media, or execute scripts creates a potential attack surface for malicious actors.
- Unencrypted Memory Store: Persistent embeddings may contain personal data that could be extracted if not properly encrypted.
- Lack of Permission Model: Third‑party plugins can request broad system access without clear user awareness.
Industry Response
Project maintainers have introduced a “security‑first” label encouraging best practices such as secret management and code reviews. Some users mitigate risk by running Clawdbot inside isolated containers. Enterprise AI vendors are monitoring the trend, emphasizing built‑in guardrails and compliance certifications as differentiators.
Future Outlook
Clawdbot’s rapid rise showcases the promise of democratized AI assistants, yet its open‑source nature also amplifies privacy and security challenges. Ongoing community efforts must focus on encrypted storage, granular permission controls, and regular security audits. As standards evolve, the balance between innovation and protection will determine whether open‑source assistants become trusted digital coworkers or cautionary examples of unchecked automation.