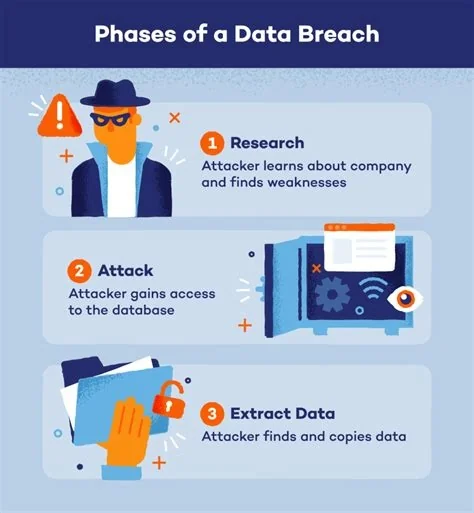
Data breaches occur when unauthorized parties access, use, or expose personal information, putting your identity, finances, and reputation at risk. The speed of disclosure, the type of data stolen, and how companies respond all determine the impact on you. Understanding these factors helps you react quickly and protect yourself when a breach happens.
Substack Slip‑up
Substack unintentionally made subscriber email addresses and phone numbers searchable for months before the issue was publicly confirmed. The delay illustrates how organizations can focus on internal fixes while leaving users unaware of the exposure.
Conduent Letter‑Flood
Millions of Americans received letters from Conduent, a government‑services contractor, warning of a breach that affected a large portion of the population. Although the exact data set remains unclear, the sheer scale shows how a single vendor can become a massive attack surface.
New Zealand Notifiable Breach Playbook
New Zealand law requires immediate notification to the Privacy Commissioner and affected individuals once a breach is discovered. This framework emphasizes that rapid, transparent communication isn’t just good practice—it’s a legal obligation.
Why These Examples Matter
Even a fictional scenario used in training mirrors real health‑sector breaches, proving that delayed decision‑making can magnify damage. The lesson is clear: swift action is critical, especially when sensitive health data is involved.
Key Takeaways
- Speed Saves – The timeline of disclosure directly influences trust and mitigation.
- Scope Matters – Seemingly minor data like emails can enable sophisticated phishing attacks.
- Regulatory Pressure Is Rising – Governments are tightening breach‑notification rules, and non‑compliance can lead to hefty fines.
- Vendor Management Is Critical – Outsourcing does not absolve a company from responsibility; thorough due‑diligence is essential.
Practitioner Perspective
Security leaders agree that preparation beats reaction. A solid breach‑response plan that defines roles, communication channels, and escalation paths serves as the first line of defense. Regular tabletop exercises turn theory into action when minutes count.
In the Substack case, pinpointing the exact data exposed proved challenging. Knowing precisely what’s compromised is half the battle, highlighting the value of comprehensive data inventories. For Conduent, clear, actionable letters that explain what’s stolen and what steps to take empower recipients and reduce panic.
Looking Ahead
As data ecosystems grow, more breaches are likely to surface. Each incident, however, pushes standards higher, regulations tighter, and response playbooks sharper. If you receive a breach notification, verify the source, follow the recommended steps, and consider a credit freeze if financial data is involved. If you run an organization, treat every breach as a rehearsal: update your response plan, involve the right stakeholders immediately, and keep communication channels open.