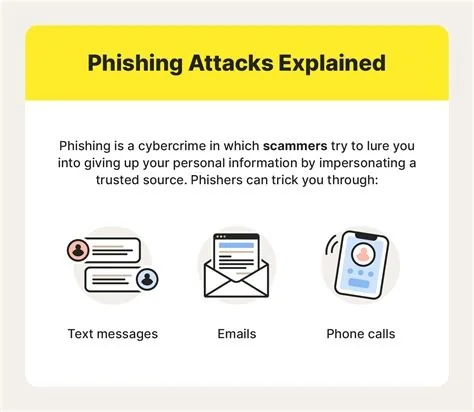
Phishing is a cyber‑crime where attackers pose as trusted brands to steal your credentials, money, or personal data. It spreads through email, SMS, instant messages, and even voice calls. You can stop most attacks by spotting the tricks, verifying senders, and using multi‑factor authentication. Below is a quick guide to recognize and block phishing today.
How Phishing Works
Common Vectors
- Email messages that mimic legitimate companies.
- SMS texts (often called smishing) that contain urgent links.
- Instant‑messenger chats that request personal info.
- Voice calls (vishing) that claim account problems.
Why Phishing Is Effective
Attackers exploit basic human emotions—fear of loss, excitement over a prize, or the desire to help. When a message looks official, you’re more likely to act without double‑checking. The sense of urgency pushes you to click a link or reply before you realize something’s off.
Top Signs of a Phishing Attempt
- Suspicious URLs: Hover over links to see misspelled domains or odd sub‑domains.
- Unexpected requests: No reputable company asks for passwords, payment details, or personal IDs via email or text.
- Spelling or grammar errors: Legitimate brands usually proofread their communications.
- Generic greetings: “Dear Customer” instead of your real name is a red flag.
Immediate Steps to Protect Yourself
- Verify the sender by checking the email address or phone number.
- Never click links in unsolicited messages; go directly to the official website or app.
- Enable multi‑factor authentication (MFA) on all accounts.
- Report suspicious messages to your IT department or email provider.
Long‑Term Defense Strategies
Combine technology with education. Use AI‑driven email filters and URL reputation services, but also train yourself and your team to recognize phishing cues. Regular simulated phishing drills can lower click‑through rates and keep awareness high.
Future Trends and What They Mean for You
Phishers are adopting deep‑fake audio, personalized spear‑phishing, and AI‑generated content. That makes attacks harder to spot, but stronger email authentication standards (DMARC, SPF, DKIM) and broader MFA adoption raise the barrier. Staying informed and skeptical remains your most reliable shield.