New AI‑powered phishing campaigns are targeting Gmail users by mimicking legitimate messages, exploiting a Gmail feature that has not yet been released, and extending the attack through WhatsApp. These sophisticated attacks combine realistic content, early‑feature manipulation, and cross‑channel lures, making them far more convincing than traditional phishing attempts for both individuals and organizations.
What Happened?
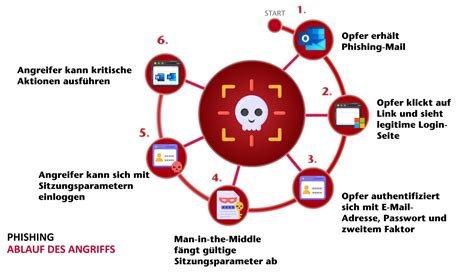
- AI‑generated Gmail messages – Attackers use advanced language models to craft personalized emails that include current topics, proper salutations, and forged Google logos. The content is so realistic that users often cannot distinguish it from genuine communications.
- Premature use of an unreleased Gmail feature – Cybercriminals have begun exploiting a forthcoming address‑change functionality. By sending fabricated “address‑change confirmation” emails, they bypass spam filters because the messages appear to be system‑generated notifications.
- Cross‑channel lure via WhatsApp – Victims receive WhatsApp messages that appear to contain Gmail alerts. The messages direct users to malicious links that capture login credentials through hidden forms.
Context and Background
Gmail processes billions of emails daily and is marketed as one of the most secure email providers. Google’s AI‑driven filters claim to block over 99.9 % of spam, phishing, and malware. Despite these defenses, attackers now leverage natural‑language generation models to craft messages that evade automated detection.
Threat actors are also monitoring upcoming product roadmaps, allowing them to weaponize features before they become publicly available. This proactive approach forces organizations to broaden their security focus beyond current vulnerabilities.
Impact on Users and Organizations
Credential theft
Compromised login details give attackers access not only to Gmail but also to linked Google services such as Drive, Calendar, and YouTube. For businesses, this can lead to data breaches, intellectual‑property loss, and the ability to send phishing emails from trusted internal addresses.
Exploitation of future features
Early targeting of unreleased functionalities demonstrates that threat actors study product announcements closely. Security teams must therefore incorporate upcoming changes into their threat‑modeling and review processes.
Cross‑channel attacks
By combining email and messaging platforms, attackers render traditional email‑only security measures insufficient. Organizations need unified‑communications protection that monitors all communication vectors.
Immediate Actions You Can Take
- Verify suspicious links: Hover over links to inspect the URL. Authentic Google links always end with .google.com or .gmail.com.
- Enable two‑factor authentication (2FA): Even if credentials are stolen, 2FA blocks unauthorized access.
- Review security alerts directly: Access the official Google login page to investigate unusual sign‑in attempts; do not respond to email prompts.
- Conduct regular awareness training: Focus on high‑risk groups such as executives, journalists, and IT staff.
- Integrate threat‑intelligence feeds: Use real‑time feeds to automatically block known malicious IP addresses and domains.
Future Outlook
The convergence of AI‑generated content, early‑feature exploitation, and multi‑channel lures marks a new era in phishing. While Google continues to enhance its filtering algorithms, the most effective defense remains vigilant human judgment. Continuous education, proactive threat intelligence, and comprehensive security strategies are essential to stay ahead of increasingly sophisticated attackers.