In 2026 DDoS attacks have grown both in size and sophistication, combining massive traffic floods with stealthy, application‑level tricks that mimic legitimate users. Organizations face record‑breaking bandwidth spikes, blended attack vectors, and faster‑evolving botnets. To stay resilient, businesses need multi‑layered mitigation, real‑time monitoring, and adaptive response plans that address both volumetric and stealth threats.
What Is a DDoS Attack?
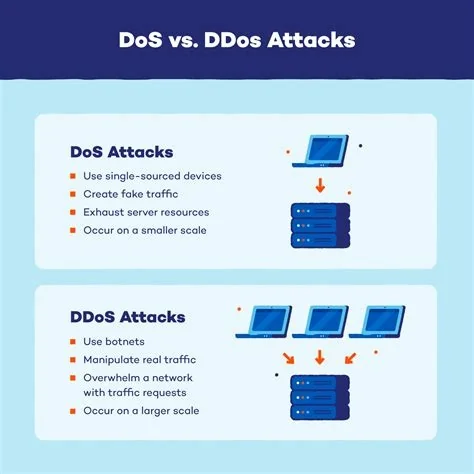
A Distributed Denial‑of‑Service (DDoS) attack overwhelms a server, website, or online service by flooding it with a massive volume of requests from many compromised sources. The onslaught exhausts the target’s ability to process legitimate traffic, effectively denying service to real users. Attack vectors include network‑level methods such as SYN floods and UDP amplification, as well as application‑level techniques that target the Layer 7 portion of the OSI model.
Recent Attack Trends in 2025‑2026
Record‑Breaking Traffic Volumes
Late 2025 saw coordinated assaults that generated traffic exceeding 300 Tbps across multiple targets. These attacks combined high‑volume network floods with sophisticated HTTP GET and TLS handshake bursts, demonstrating how attackers can blend volumetric and application‑layer techniques to bypass traditional filters.
Stealth DDoS Techniques
Attackers increasingly embed malicious traffic within normal‑looking requests, such as routine API calls or standard web page loads. This “stealth DDoS” approach makes detection harder for signature‑based systems, as the traffic mimics legitimate user behavior while exhausting server resources like CPU, memory, and database connections.
Evolving Defense Strategies
Traffic Scrubbing and Diversion
Modern DDoS mitigation routes inbound traffic through scrubbing centers that identify and drop anomalous patterns before they reach the target. Distributed networks of scrubbing nodes filter traffic close to its source, reducing latency for legitimate users while stripping malicious packets.
Rate Limiting and Behavioral Analytics
Applying request‑rate thresholds and leveraging machine‑learning models helps distinguish normal user activity from attack traffic. This tactic is especially effective against stealth DDoS attacks that blend in with legitimate usage patterns.
Anycast Routing
Anycast distributes traffic across multiple data centers using the same IP address, diluting the impact of a concentrated flood and improving resilience by routing users to the nearest healthy node.
Hybrid On‑Premise and Cloud Solutions
Combining edge‑based appliances with cloud‑based scrubbing provides layered protection for both internal networks and public‑facing services, ensuring that attacks are mitigated at multiple points in the delivery chain.
Business Implications
Even brief outages can erode customer trust and cause significant revenue loss, particularly for e‑commerce platforms that rely on real‑time transactions. Because DDoS attacks are criminal offenses under statutes such as the Computer Fraud and Abuse Act, organizations may face regulatory scrutiny if they fail to implement reasonable security measures. Additionally, reliance on shared cloud providers introduces supply‑chain risk, where a single vendor attack can cascade across multiple downstream customers.
Best‑Practice Checklist for 2026
- Assess Exposure: Conduct a baseline audit of all internet‑facing assets, including APIs, DNS servers, and IoT endpoints.
- Select a Multi‑Layer Provider: Choose a mitigation partner that offers both network‑level scrubbing and application‑layer inspection with a globally distributed node network.
- Implement Real‑Time Monitoring: Deploy dashboards that surface traffic anomalies within seconds to enable rapid response.
- Test Incident Response: Run tabletop exercises and simulated attacks to validate playbooks and ensure coordination across security, networking, and business units.
- Maintain Redundancy: Use anycast DNS and multi‑region deployments to spread risk and eliminate single points of failure.
Future Outlook
Attackers are expected to incorporate AI‑generated traffic patterns that adapt in real time, further blurring the line between legitimate and malicious requests. Static defenses will become increasingly inadequate. Continuous investment in adaptive, high‑capacity mitigation—paired with rigorous monitoring and response planning—will be essential to protect digital services in an ever‑more hostile internet environment.