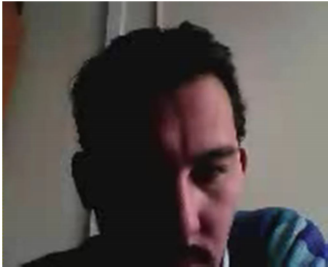
Russian (?) Hacker/Spook
While investigating an attack from a botnet installed on a number of sensitive servers the CERT team uploaded their own Trojan with a tempting name, “Georgian-Nato Agreement” that had the capability to control the hackers webcam and send photos of the perp back to home base.
The bots were distributed by infected Georgian News websites, where specific pages, presumably of news that was of interest to government officials, were loaded with the malicious payload.
Once infected by the targeted attack the command and control centres had full control of the compromised systems. As it was a targeted attack, with custom code, none of the standard Anti-Virus tools were able to detect the malicious software.

Russian (?) Hacker
Automated searches of the infected system for “sensitive words”, such as NATO, DOD Russia, CIA, Obama and FSB, in MS Word, XLS, PPT and PDF documents kicked off and uploaded anything found of interest to internet dumping grounds. It also searched for remote desktop configuration files (pbk files) and was able to scan the rest of the attached network. The bot had access to the built in video and microphone functionalities.
Command and Control servers were spread across the globe, including the US, France and Germany, and would cycle to a new S&S when it look like the original was discovered.
In total 390 servers were infected, with 70% of them in Georgian and the rest spread throughout Europe.
While installed the bot continually updated itself, moving from the original version 2.1 to 5.5 over a ten month period.
The Georgian CERT team believe they traced the hacker back to the Russian Official Security Agencies, including via his IP, emails, and the built in backup command channel in the event the bots lost all communication to primary channels.
With the US and Israeli governments opening admitting to attacking other countries with Cyber tools and now Georgia supposedly catching the Russians with the hand in the cookie jar, it seems Cyber War is real and ongoing.
Read more here in the English version of the CERT summary: http://dea.gov.ge/uploads/CERT%20DOCS/Cyber%20Espionage.pdf
And if you are concerned about targeted attacks, code that no anti-virus company has seen before, you might want to talk to the boys at Trend Micro about their Deep Discovery product. It inspects the network traffic so you can identify traffic talking to external command and control centers. Or FireEye which does something similar. If one thing Stuxnet, Flame and this incident demonstrates to us is, Anti-Virus is not enough.
